Multi-Factor Authentication – Q&A and Troubleshooting
1. What is the secure device?
- The secure device has the following properties:
- You have an own account on your device that you do not share with others.
- Your account is protected by a password, PIN, fingerprint, or similar method.
- Access to the device is restricted, i.e. random persons cannot access it.
- These following devices qualify as secure:
- Computer in a lockable office with the school version of Windows.
- A laptop on which you work mostly on your own and usually carry it with you. Any other users on the laptop have their own account.
- Computer at home if you have a separate account on it.
- A mobile phone that you do not share with others.
- Examples of devices that do not qualify as secure:
- Computer in computer classrooms.
- Cizí počítač včetně počítačů Vašich známých.
- A home computer where you share the same account with other family members.
- Mobile phone that you lend to children or grandchildren for games.
Secure device information is stored in a web browser. If you use multiple browsers, you need to confirm each device separately. If the browser is in incognito or private mode, the secure device information is cleared when it is closed.
2.I do not have a suitable mobile phone. I do not want to use a private mobile phone.
We will install an application for generating one-time verification codes on your computer and pair it with your account in the study information system. It has a disadvantage – you can only log in from this one computer, or else, you must be able to check the verification code generated on the primary computer when you log in on another computer.
3. I have a new mobile phone, how do I transfer the code?
There are more options:
- Back up in the code generation application. Install the same application on the new mobile phone and choose the recovery of saved secret passwords.
- You have printed a QR code and have it available. Install the one-time password generating application on your new mobile phone and take a photo of the QR code in it.
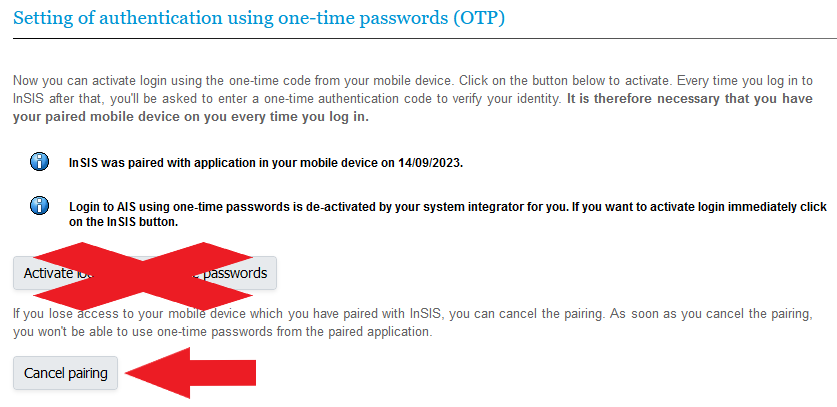
- In InSIS, pair the new mobile phone with your account. This applies only to users with the optional use of one-time passwords. You log in to InSIS using the application in the old mobile phone. In the application, in “One-time Password Authentication Setting (OTP)”, temporarily disable the use of one-time passwords and cancel pairing your old mobile phone with your account. Then pair the new mobile phone with your account.
- You cannot use any of the previous methods. Request the administrator to suspend MFA for InSIS. After logging in, FIRSTLY, unpair the original device in the “One-Time Password (OTP) Authentication Settings” and then set up MFA again for the new device.
4. I came to school without my mobile phone.
- You are working on a secure device. If you have identified your work computer in your office as a secure device, there is a high probability that you will not have to enter a verification code today.
- You will return home for you mobile phone. Sometimes this is the simplest solution.
- You have paper with QR code printed in your office. Ask a trusted colleague to take a picture of your QR code into his or her application to generate one-time passwords and help you log in. After logging in, the colleague should delete your entry from his or her application.
- You will request to temporarily disable multi-factor authentication. The administrator can temporarily disable multi-factor authentication for you, but for a maximum duration until the end of the current day.
5. My mobile phone battery is dead.
The easiest way is to borrow a charger and charge your phone. If this is not possible, use one of the solutions in case of forgotten mobile phone.
6. I managed to pair my account with my mobile phone, but I am not able to log in now.
There may be different reasons. So far, we have encountered the following ones:
- Wrong password – the InSIS checks the password only after entering the code. Moreover, it displays the same error message whether the password or the code is wrong. So you do not know whether you entered the wrong password or the wrong code
- Wrong time on the mobile phone – the time varied by about 2 minutes and the user was unable to log in. We solved this by setting up automatic time synchronization on your mobile.
7. What are the security benefits of the multi-factor authentication?
Multi-factor authentication protects against most password leaks, such as:
- a fraudster monitors your keyboard as you enter your password
- a fraudster manages to persuade you to enter a password on his or her website (successful phishing)
- you use the same password on multiple servers and the password will leak from some of them
- you accidentally type the password instead of the username and a fraudster will then misuse it
- a fraudster installs a keylogger on a computer (e.g. in classrooms)
8. What security risks remain?
Multi-factor authentication is significantly more secure than password-only login. However, it may be breached. Here are the two most common and simplest ways:
8.1 The attacker installs his or her software on the computer where the user logs on to the study system.
First of the 10 Immutable Laws of Security says: If a bad guy can persuade you to run his program on your computer, it is not your computer anymore.
Specifically, you log in to the study system and the fraudster then will control the keyboard for you, enter commands for you.
Basic recommendations:
- Use an updated antivirus program.
- Do not download applications from suspicious sources.
- In e-mail, do not click on attachments that you did not expect.
- Update your operating system and other applications regularly.
- Encrypt your disks on portable devices (e.g. laptops).
8.2 The attacker physically gets to the computer where the authorized user is logged in to InSIS.
Individual operations are usually protected by multi-factor authentication when managing a bank account. In InSIS, however, there is only a login – the attacker comes to the logged-on computer and continues as a legitimate user.
Basic recommendations:
- Do not leave your computer unattended.
- Be sure to log out of the computer when leaving the classroom.
- When leaving the computer, lock the operating system – Windows key combination Win+L. Log out as the case may be.
- Set a sleep mode, e.g. after 30 minutes of inactivity. A password is required to resume from the sleep mode. You can also try the Dynamic Lock.
9. Restoring the InSIS account pairing with the authentication application
Typically used in a situation when you have either uninstalled the authentication app from your device or accidentally removed your InSIS account from the authentication app, and you do not have access to the QR code from the original pairing.
Note: In order to restore pairing, it is necessary to first request the HelpDesk dept. to suspend multi-factor authentication for your InSIS account. You can send the request from your school email, a verified private email, or visit in person.
>> Procedure for restoring pairing when multi-factor authentication is suspended (click to expand the instructions) <<
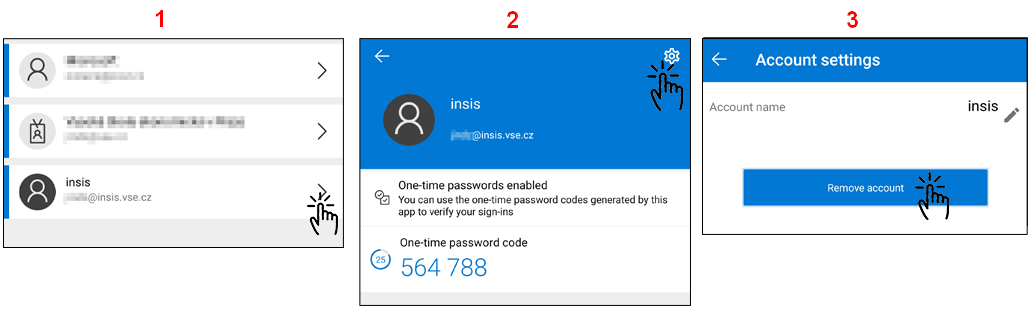
1. Remove your InSIS account from the authentication app (below is an example from Microsoft Authenticator):
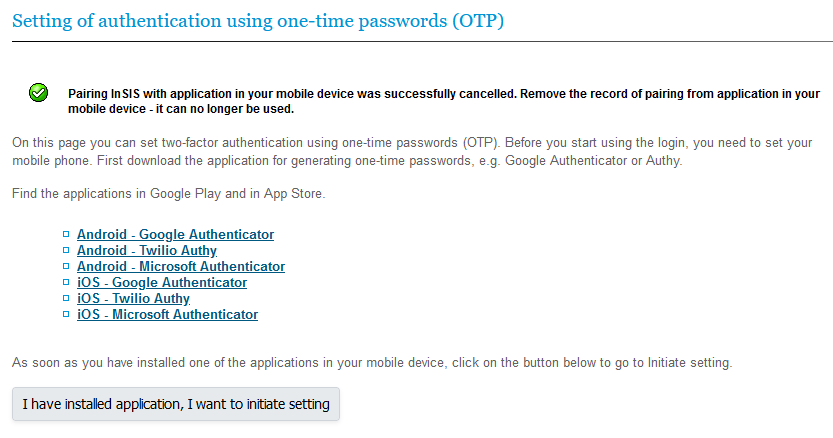
2. Log in to your InSIS account and continue to the Information System Set-up, and then to the Setting of authentication using one-time Passwords (OTP):
4. InSIS informs you that the pairing with the application has been canceled. You can now start a new pairing process by clicking on I have installed application, I want to initiate settings and following our set-up guide here.