Spam, Fraudulent E-mails
- Fraudulent E-mails (Phishing, Malware), Junk Mail (SPAM)
- Malware Protection
- Phishing Protection
3.1 How to Defend against Phishing?
3.2 Phishing Test
3.3 I Received a Phishing E-mail
3.4 I Fell Victim to Phishing. What Should I Do? - Unsolicited Commercial Messages (Spam)
4.1 Report Spam (Way of Legal Defense)
4.2 SPAM Is Not Marked as SPAM
4.3 The Message Is Incorrectly Classified as SPAM
1. Fraudulent E-mails (Phishing, Malware), Junk Mail (SPAM) [menu]
Here are the most common ways how email can be misused.
- When malware is spread, an attacker’s goal is to install malicious software on your computer.
- When phishing, the attacker tries to obtain sensitive data such as passwords or credit card numbers.
- For unsolicited commercial messages (spam, junk mail), the goal is to gain customers or otherwise support the sender’s business.
- Nigerian e-mails or Scam419 [only in Czech] – an unknown person has inherited, acquired or even manages someone’s property worth tens of millions of dollars and needs help transferring it from the country. During the communication, they try to extract money – notary fees, transfer fees, etc. from you. Alternatively, they want to access your account and launder money through it. In English, the name Advance-fee scam is used.
2. Malware Protection [menu]
Two basic techniques are used: either the e-mail contains an infected attachment (executable programs, documents,…) or the e-mail contains a link to a page from which the user downloads the infection.
- Do not open attachments from suspicious or unexpected senders.
- A regularly updated antivirus program on your computer will also help.
When an e-mail passes through mail servers, messages with infected attachments and messages with executable attachments (e.g. .exe files) are blocked. Malware can be part of the e-mail’s own text (html text with JavaScript) – mail programs ignore these executable parts. This makes it safe to turn off antivirus add-ons in Outlook.
3. Phishing Protection [menu]
Fake sites can be credible and difficult to identify, and e-mail often uses a variety of social engineering methods. The most common trick is to make you feel that you need to log in to your account right away – otherwise you will lose your money or your account will be blocked. The content of the e-mail often pretends to come from popular social networks, auction sites, online payment portals, government agencies or IT administrators.
In the Phishing article How to Recognize It and Not ‘Fall for It’ [only in Czech] (“Jak jej rozpoznat a „nenaletět“), you can learn how to recognize a phishing e-mail and a phishing website.
3.1 How to Defend against Phishing? [menu]
- Ignore suspicious emails.
- Use the official website to log in to the bank and other servers, do not click on any links in the e-mail, use the official website to log in.
- Keep in mind that no institution, let alone a banking institution, will ever ask you for login details by e-mail. Be careful.
- Keep in mind that phishing may not only be related to the topic of electronic banking, but it is also, for example, an attempt to obtain a password to e-mail or other services.
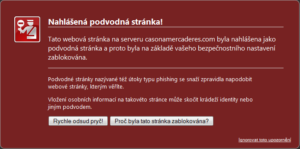
- Be careful before logging in or registering anywhere. Check the address on the browser’s address bar, make sure you are using a secure connection. Do not log in to the site if the browser has previously reported a certificate error.
- When phishing comes from abroad, you will usually recognize it due to bad Czech/English, atd.
- If you access an already known phishing page in your browser (someone has reported it), a warning will be displayed.
3.2 Phishing Test [menu]
![]() Phishing test (1): Test how many emails Chuck Norris received 🙂 are legitimate, in your opinion. The phishing test [only in Czech] was created by the Slovak security team.
Phishing test (1): Test how many emails Chuck Norris received 🙂 are legitimate, in your opinion. The phishing test [only in Czech] was created by the Slovak security team.
Phishing IQ Test from SonicWall.
Examples of phishing, articles on phishing cases:
- Examples of Phishing from the University of West Bohemia [only in Czech]
- Cases of Phishing on the Hoax.cz Website [only in Czech]
- Articles about Phishing on Lupa.cz [only in Czech]
3.3 I Received a Phishing E-mail [menu]
You can report a phishing website to:
- Google – blocking in Chrome, Firefox, Android, iPhone and more
- Microsoft – blocking in Office 365, Edge, Internet Explorer,…
Please notify us of cases where phishing concerns VŠE. Check the TODO page to see if this particular case is already listed. If not, send a notification to helpdesk@vse.cz – preferably including the headers of the fraudulent e-mail.
3.4 I Fell Victim to Phishing, What Should I Do? [menu]
I.e. you entered your username and password on a fraudulent website.
- Do not panic!
- The attacker has your login details – the first step is to change the password in the school system (in InSIS).
- Think about where else you have the same password – your password may be disclosed in a shorter or longer period of time and someone can it with your accounts elsewhere (banks, shops, private mail,…). Change the password on these systems as well.
- Call or send a message to the Help Desk of the Informatics Center. They will advise and help you there. They can also find out if your login details have been misused by someone (e.g. if someone made any unauthorized change in the study system).
4. Unsolicited Commercial Messages (Spam) [menu]
Unsolicited commercial messages are defined in Act no. 480/2004 Coll., Which is based on the European Community Directive no. 2000/31/EC. The term commercial communication refers to all forms of communication intended for the direct or indirect promotion of goods or services or the image of a natural or legal person’s business.
The seller can send a commercial message if:
- it is addressed to his customer,
- who has not refused to receive similar messages in the past,
- the messages concern similar goods or services,
- the recipient has given his prior consent.
Sending an e-mail for the purpose of propagating a commercial message is prohibited if
- this is not clearly identified as a commercial communication,
- he hides or covers up the identity of the sender on whose behalf the communication takes place; or
- it is sent without a valid address to which the recipient could directly and effectively send information that he does not wish the business information to continue to be sent to him by the sender.
Please distinguish spam from commercial communications and other potentially annoying mail. An analysis of messages marked as spam shows that in about half of the cases it is not spam.
We do not wish and will not mark intra-school mail communication as SPAM.
If there is an unsubscribe option in the e-mail, it is usually not spam, but a business offer. You could have subscribed, someone else could have subscribed you, you could have subscribed with someone and they had the condition that they can sell the contact database.
| Invitations to conferences, requests to fill in questionnaires, offers of publication in professional journals are also among the commercial messages. If you send them – do you comply with the requirements of the law? |
Reputable companies in their business communications refer to the possibility of unsubscribing. Unsubscribe if you do not wish to receive these e-mails and do not mark them as SPAM. Even if they bother you. There are three reasons for this:
- you will not restrict other users who wish to obtain this information via e-mail,
- you will reduce the number of forwarded and processed e-mails,
- you will act responsibly towards the company that sends these messages.
If you come across a non-functional or very suspicious option to log out, it is usually SPAM – senders try to go around antispam checks.
4.1 Report Spam (Way of Legal Defense) [menu]
The way of legal defense against spam is slow. In other ways, however, you will not achieve that the spammer suffers high financial losses or the spammer’s company ceases to exist. Read the following articles describing the success of the legal way:
- Last year Czech Spammers Received Fines Totaling of 147,000 CZK. An article from 2013 [only in Czech].

- Record Fines for Spam: eMarketing CZ and Traffic7 Will Pay 1.5 and 1.9 Million CZK, Respectively. An article from 2015 [only in Czech].
- Purchasing a Spam Distribution Is Not a Good Idea. An article from 2015 [only in Czech].
You can report the Czech spam to the Office for Personal Data Protection. They have a simple complaint form [only in Czech] on their website. You can complain as a natural person or as an employee performing tasks for a legal entity.
You can read about the details of the Czech legislation in the article New Regulation (of Fight against) Spamming [only in Czech].
How to complain about spam from Slovakia is described in the following articles:
- How to Defend against Spam and Definitely Report it to the Authorities [only in Slovak]
- post from discussion on root.cz [only in Slovak]
4.2 SPAM is not marked as SPAM [menu]
The article I Have Spam in the Inbox. What Should I Do? describes how to improve the success of spam detection.
4.3 The Message Is Incorrectly Classified as SPAM [menu]
The article I Found a Regular E-mail in the Spam Folder. What to do? describes what options you have to influence incorrect SPAM classification.